- Standards for encrypting passwords in configuration files?, How can I decrypt data with Java, without hard-coding the key?, Password in. @C.Ross, Hmm, I thought I already did address all of the issues in the question. In short: encrypting the password in the config file is pointless, unless you have a better place to store the.
- A simple way of doing this is to use Password Based Encryption in Java. This allows you to encrypt and decrypt a text by using a password. This basically means initializing a javax.crypto.Cipher with algorithm 'AES/CBC/PKCS5Padding' and getting a key from javax.crypto.SecretKeyFactory with the 'PBKDF2WithHmacSHA512' algorithm.
- Encryption Passwords In Java Property Files Free
- Encryption Passwords In Java Property Files Download
- Decrypt Encrypted Password
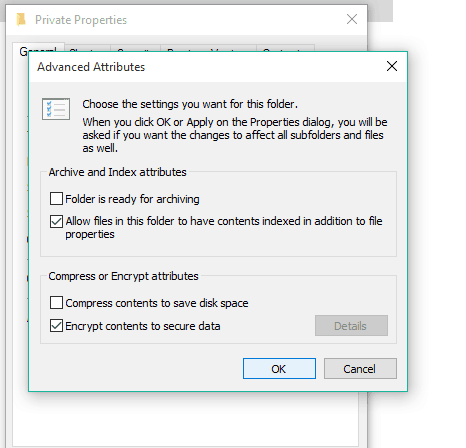
- Encrypting File System Windows 10
Typical Java backend applications need to integrate with existing 3rd party services. In most cases, calls to these 3rd party services are authenticated. Frequently, Java applications are required to use login credentials for authenticated calls: A username and a password.
This scenario raises a problem: How can we store the password needed for calling the 3rd party service? We could store it in a properties file, but then everyone with access to the properties file learns the password. We could provide the password as a command line parameter or environment variable, but then everyone with access to the startup script learns the password. We could hard-code it in our application, but then everyone with access to the JAR file learns the password. We could encrypt the password using a master key, but then we have the same problem again: How to store the master key?
I am very new in Spring framework and I am using Spring framework to manage my database connections and so on. Applicaiton reads my db connection parameters from a property file. The thing I need is to store my connection password in property file as encrypted. Here is my datasource xml file. This tutorial will show how to encrypt a password text stored in a properties file and retrieve the password later through a decryption process. JSypt will be used for encryption and decryption task. Apache Commons Configuration project will be used to easily manipulate properties file. Encrypting Passwords in Configuration Files. Encrypting Configuration Passwords on Enterprise Servers. Most enterprise servers, like JBoss, Glassfish, WebSphere, and WebLogic, have proprietary ways to set up password encryption. You might have to install 'Unlimited Strength Jurisdiction Policy Files' from the Oracle site for your Java. Encrypt/Decrypt String in Java Property File Hi all, I think It would be very useful to know how to encrypt/decrypt a password/general string when we store it in flat file. In java the common way to store settings properties, like a username or a password, is to use the Java Property File class using the standard methods: setProperty. Note that the database password is encrypted (in fact, any other property could also be encrypted, be it related with database configuration or not). How do we read this value? Like this: /* * First, create (or ask some other component for) the adequate encryptor for * decrypting the values in our.properties file.
The common solution is to use a secure data store provided by the operating system. Our application runs on Windows Server, so we use the Windows Data Protection API (DPAPI) for protecting our secret passwords. This blog post shows how to use the DPAPI in Java applications.
windpapi4j
There are a few Java wrappers for the Windows Data Protection API (DPAPI) available. We went with peter-gergely-horvath/windpapi4j, because it’s simple, only a few lines of code, and it’s available on GitHub under the LGPL license.
windpapi4j is available as a Maven dependency:
The API is very easy to use:
The output of the example code on Windows would be:
We can now store the encrypted string in our properties file, and call decrypt() in our application to get the secret data.
Encryption Passwords In Java Property Files Free
Which key does Windows use to encrypt our data?
As you might have noticed, we call encrypt() and decrypt() without providing the encryption key. The key is managed by the Windows operating system and not by our Java application.
Windows uses a randomly generated master key to protect the data. The master key is encrypted with the user’s login password and stored in the user profile. When the user changes the login password, Windows automatically re-encrypts the master keys. Additionally, Windows keeps a “credential history” in the user profile so that it can restore data even if updating the master key failed.
The application must run under the same user who encrypted the data. Only then can our application decrypt() the data from the properties file. If the application runs under another user, the data cannot be decrypted. If the application runs on another machine, the data cannot be decrypted unless the same user profile is available on the other machine.

How to maintain the properties file
Our application is implemented as follows: When the administrator installs the application and starts it for the first time, he must create a configuration with the plain text password. The application then generates a properties file containing the encrypted version of these passwords. Once this is done, the administrator may delete the plain text configuration. Now the application runs using the generated properties file, and the plain text passwords are no longer stored anywhere on the machine.
TL;DR
The Windows Data Protection API (DPAPI) provides a convenient way of protecting secret data. The encrypted data can be stored in a Java properties file. A Java application can read the properties file and call the DPAPI to decrypt the data. The Java application does not need to maintain the encryption keys, as this is done by the Windows operating system.
Safe icon above from http://iconleak.com.
Encrypt a passwordTag(s): Security
Encryption Passwords In Java Property Files Download
Transmit a password with MessageDigest
Message digests are secure one-way hash functions that take arbitrary-sized data andoutput a fixed-length hash value.Decrypt Encrypted Password
A One-way hash function computes a number from a given data. There is no way to decrypt that numberto retrieve its original value. The only way is to compute again the same value and check if the resultis the same than the previouly computed one.
In this scenario, the user sends a password to the server (through a secure connection). The servercomputes the computed hash code with the stored hash, if it's the same then the password is correct.The password is never stored in the database.
The output is :Store a password in a properties file
 If an automated task needs to log in then you must provide a username/password. Since it's an automated taskyou can retrieve the username/password from something like a properties file. A security bestpractice is to never store a password in plain text, you must encrypt it using an appropriate algorithm.The javax.crypto package provides those algorithms andAES is one of them.To retrieve the original value from an encrypted string, you need to use a
If an automated task needs to log in then you must provide a username/password. Since it's an automated taskyou can retrieve the username/password from something like a properties file. A security bestpractice is to never store a password in plain text, you must encrypt it using an appropriate algorithm.The javax.crypto package provides those algorithms andAES is one of them.To retrieve the original value from an encrypted string, you need to use a secret key habitually stored in a different location than the user/password file.
secret key habitually stored in a different location than the user/password file.In this scenario, a process gets its user and password from a properties file. The password is crypted, the processuses a 'key' stored in a different secure location to decrypt the password. The password is sent to the server forauthentication by comparing the computed hash of the received password with the hash code stored for this user inthe database.
Encrypting File System Windows 10
In this HowTo, a key file is created during the encryption process if the specified key file is not found.